Safety is a DeFi !

Intelligent identity and access management offering ergonomics, simplicity, save up and reliability
Your Smartphone as unique enrollment, authentication and validation terminal.
One authentication process to access all authorized resources and applications that means no need to remember multiple login and passwords.
Managing multiple levels of security access independent from each other, with established communication “tunnel” for each level and for each connection, ensuring total imperviousness of each connection.
Virtual Office established for each connection involving all applications and authorized data, no data is locally stored on each disconnection.
A company LAN and WAN access to the SI totally secure authentication treated in three separate channels SMS GPRS/3G-4G, DTN with five independent factors including strong geo localization.
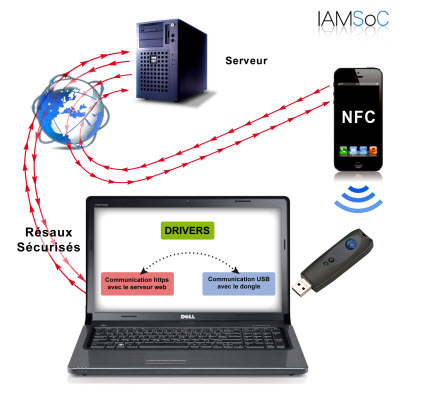
Our Identity Management and Access IAMSoC platform is a cyber security solution tailored and unique to each user and for each information system in the way we combine various proprietary technologies to manage the entire SI. It allows our clients to manage physical access through an encrypted electronic lock coupled to an IP camera.
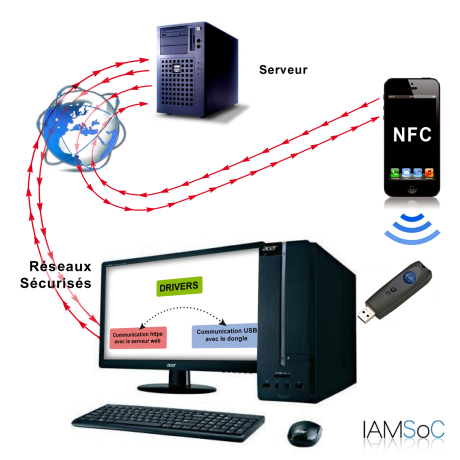
IAMSoC is a security platform centralized at a single point of governance for managing identities and access LAN and WAN to information system (IS) and cloud through one or more mobile devices with transponder system based on several independent authentication factors: biometrics, geo location, unique ID, with a proprietary encryption and a single both dynamic and random virtual keyboard for each application, and having a presence management in real time and continuously.
IAMSoC is by definition a continuous innovation process:
- By its very independent authentication factors:
- A unique ID
- A data encryption unique to each user with correlation with GPS position repudiation value
- A unique virtual keyboard with dynamic, random, and ephemeral encryption for each user
- A biometric identification,
- A password
- Due to its innovative architectural concept Amastan is designed to centralize governance at one point of the SI, which among other IAMSoC management ghosts’ profiles and real-time access rights, and its authorization management backed by a virtual board system that is formed only when the person logs in to access its resources.
- Due to its technology that generate encrypted temporary identifiers used to secure access to resources.
- By correlating various information or devices to prevent unauthorized use, witch on top of a biometrics authentication uses geo location to check authentication. A Repudiation system is also used in case an anomaly occurs during authentication process.
- By its transponder link used to enhance security and interrupts communication immediately if a customer is away from his PC.
- By using the DTN technology that allows management of real-time continuous presence

IAMSoC advantages:
- A combined technology designed to defeat all technical interception known today as usurpation: Social Engineering, Man in the Middle (MITM) Virus (Trojan) Screenschot, Watering hole.
- A Federation and sharing of identity, allowing easy reuse of identities across different services,
- A mobile ‘’Swiss army knife” authentication terminal to limit profusion of authentication devices side effects,
- The Audit and ongoing reporting of user activity to ensure compliance with the rules and contribute to compliance
- An administration Base, to pool authentication systems, sharing directories and actually making interoperable information systems, which limit the profusion of identification solutions and access to management information systems
- A real-time continuous presence managing module which easily ensures presence of the carrier in a defined space and its real time position allowing exclusion zones protection
- Instant messaging with a single random SoConect encrypting to each user
The advantage of Amastan system is its unique identification and authentication process, which allows to link with a unique known identifier ensuring a high level of privacy and security as well as the inviolability of identity avoiding identity fraud according to all methods known to date.
It defines a resources access, acceptable and adaptable means of identification and authentication based on the confidence that can be given to means of authentication depending on the level of clearance required.
It secures the in-depth information system on potential attacks guaranteeing both the monitoring, detection and response.
It responds to targeted attacks collected by Social Engineering (facebook, linkedin,) using IDs and dynamic code unknown by the user randomly run in infinite combination.
It offers an optimum level of safety in the state of the art, cost control, user friendly, and optimization of working time, responsiveness, monitoring, and audit reporting.
Areas of Application:
The centralized security IAMSoC application designed and developed by Amastan finds its place in organizations (SMEs, Administrations, cloud ....) that need safely access to internal or through web information without risk.It offers optimum security with several independent authentication factors ensuring access to critical and relevant business information in respect of the importance of visibility and control for the rights and permissions of each and it allows managing all movements (input, output, presence) of people in real and continuous time with certainty.
Administrations :
- Presence and Secure Areas access management
- Local and Remote SI access management with Defense Level Accreditation
- Access and Secure Areas management (Ministry, Embassy, Military Zones, Nuclear Power Plants, Port Areas, etc.)
- Hospitals: Presence control, local and remote access to resources, management (Medical Records)
- authorization level, secure proximity messaging for care staff and patients inside hospital zone and at home (Dialysis, Organs Waiting Registry, Monitoring, etc.)
- Museum’s inside information and security access
- Airports: VIP Lounge
Schools and Universities Institutions :
- Presence and access management to facility
- Zone management: Library, teacher’s Room, Dormitories, Canteens, University Restaurant, and Infirmary
- Secure local and remote access on site and national level to the SI resources
- Special Events
- Encrypted proximity messaging to target group or individual (Classes, etc.)

Games websites :
- Poker: allows site to defend against classical fraud problem of several players who band together at the same location to open play in the same game against other remote players
Privates Clubs :
- VIP access management with secure door, identifying, members’ presence control and attendance in real time
- Secured customizable messages, product launches, private events, etc.
- Secure reservations through BanKrypt Module
- Secure customizable messaging for product launches, private parties, etc.
- Same location member’s identification and personalized invitations sending through circumstantial MySoLink Module
SMEs :
- Presence and physical access to the company management
- Identity management and local and remote access management to the company’s IS for sales team, telecommuting, etc.
- Secure access client administration
- Gas Cards and Toll management
- Totally secure geo localized messaging
Hospitality :
- Room Reservations
- Secure client access management: rooms, authorized or forbidden areas
- Validation of internal expenses: Restaurant, Bar, Mini Bar, Spa, Parking, Laundry Bags ,Room Service, etc.
- Check in, Check out management
- Loyalty Cards and Members Profiles management
- Proximity personalized invitation messaging with discretionary coupons offers
Shows, Exhibitions, Corporate or Cultural Events :
- Access Management
- Proximity messaging with broadcast of targeted or general information on site and nearby


 K. Jabbar
K. Jabbar